Nearly half of stolen crypto remains unspent, data shows
Roughly 46% of hacked funds sit idle on-chain, suggesting opportunities for post-incident recovery, analysts at Global Ledger say.
Hackers are quick, but the systems chasing them are still catching up. A new report by blockchain intelligence firm Global Ledger, based on hundreds of on-chain incidents, shows that in many cases, stolen funds land at laundering destinations before the hack is even publicly disclosed.
On average, it takes 43.83 hours from the initial on-chain breach until the incident is reported by either the victim project or a third-party investigator, per the report shared with crypto.news. Hackers, meanwhile, tend to move stolen funds to the first identified entity, such as an exchange, a crypto mixer, or a decentralized finance protocol, within 46.74 hours.
The longest delay, however, is the window between public disclosure and the attacker’s interaction with a laundering service, which averages 78.55 hours, suggesting that funds are often already on the move well before a hack becomes widely known.
‘No clear playbook here’
In total, Global Ledger’s researchers measured four key timelines across hundreds of incidents. The time from breach to fund movement, from breach to reporting, from breach to first entity interaction, and from public disclosure to laundering activity. Each lag also tells its own story.
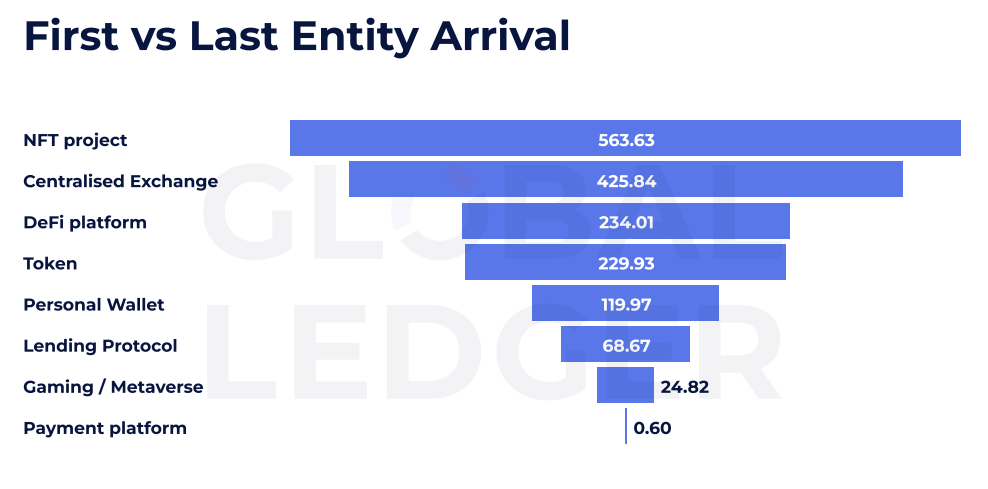
Attacks targeting NFT projects, for example, show the slowest fund movements. On average, it takes 563.63 hours — or nearly 24 days — for funds from these exploits to move from the first to the last known entity in the laundering chain. That’s more than double the average lag seen in centralized exchange-related hacks, which clock in at around 425 hours.
Global Ledger co-founder and CEO Lex Fisun told crypto.news in an exclusive commentary that the long delay — in case of NFTs — isn’t just about low liquidity as these tokens are “unique and harder to offload quietly.”
“There’s no clear playbook here, laundering usually involves wash trading or social engineering. Remember The Idols exploit, where the attacker drained $340,000 in stETH but got stuck with the associated NFTs.”
Lex Fisun
The report highlights how laundering paths vary depending on the type of project exploited. DeFi platforms and tokens typically see funds move through laundering channels within 230 hours, while payment platforms show the fastest turnaround: just 0.6 hours on average. Gaming and metaverse exploits are also among the quicker flows, moving in under 25 hours.
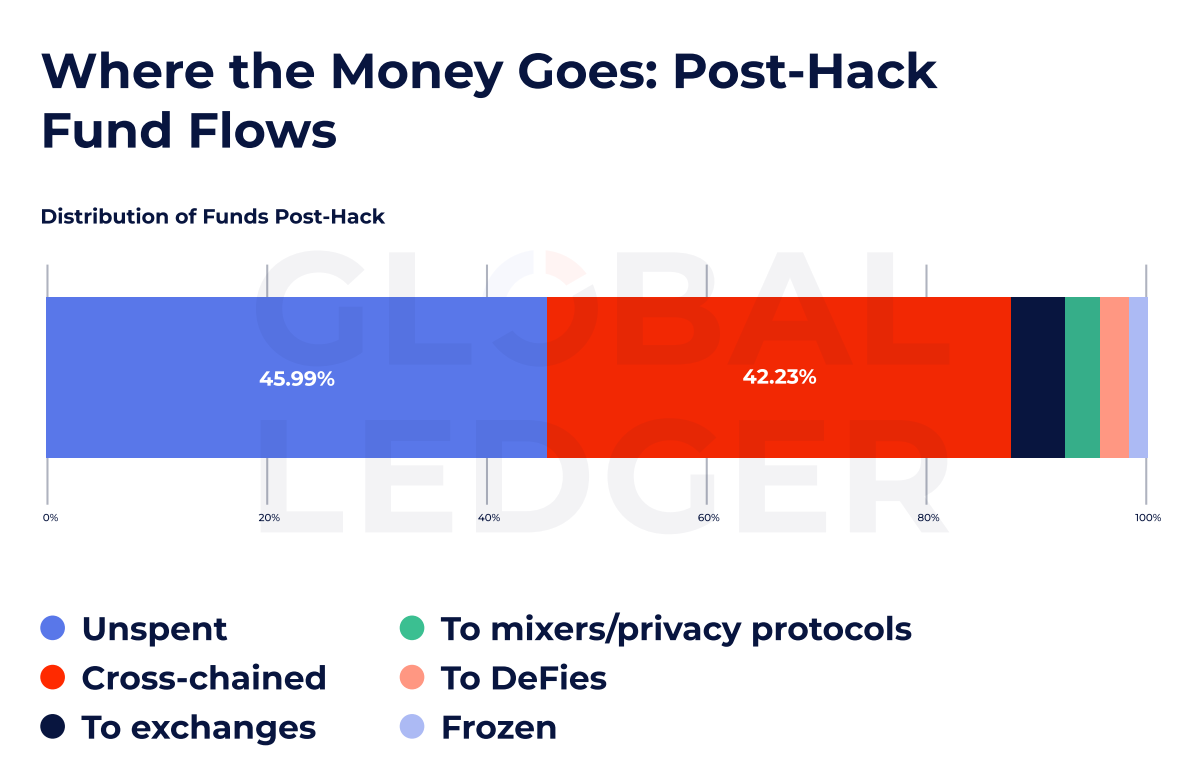
Despite the speed and fragmentation of fund flows, a surprising amount of hacked assets remain untouched. According to the data, nearly 46% of stolen funds are still unspent, suggesting significant opportunities for ongoing tracking and potentially recovery, long after an incident occurs.
Cross-chain traces
While many funds sit idle, a growing share is slipping through harder-to-trace cross-chain routes. The report shows that 42.23% of stolen funds were moved across chains, bypassing chain-specific monitoring systems.
Fisun explained that cross-chain bridges “have already become one of the top money laundering tools” for slipping past chain-specific monitoring. And while repeated abuse could draw AML scrutiny, the Tornado Cash case proves one thing: “sanctions shift tactics, not demand,” Fisun added.
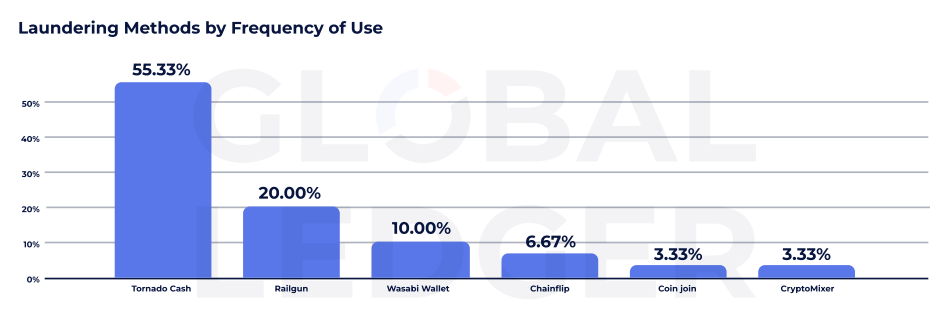
Global Ledger’s data also shows Tornado Cash remains the dominant laundering protocol, used in more than 50% of cases tracked by the firm. Despite U.S. Treasury sanctions in 2022, and mounting pressure from regulators globally, the service continues to play a central role in post-hack laundering.
Its use spiked again after a U.S. court ruling overturned the sanctions on constitutional grounds in 2024.
Other privacy tools are also gaining momentum. Railgun, for instance, was used in 20% of cases, while Wasabi Wallet appeared in 10%. Chainflip, CoinJoin, and CryptoMixer were each involved in less than 7% of laundering flows, the data shows.
Attackers getting smarter
Fisun noted that slower flows through centralized exchanges — now averaging more than 425 hours — don’t necessarily reflect better compliance alone.
It’s both, the Global Ledger CEO said, adding that a slower timeline “is not a glitch, it’s by design” as attackers split assets, hop chains, and use privacy protocols to move stolen funds through CEXs that “try to delay flows that look shady.”
Only a small portion of funds are frozen by enforcement or compliance teams. The report suggests that real-time responses remain rare, even as analytics and monitoring tools advance.
While the numbers point to continued challenges, they also underline where defenders can gain an edge. The time gaps — sometimes measured in days — show that there’s still space to act before stolen funds fully disappear.