Suspects in $14m Holograph hack arrested by EU authorities
Police in Italy and France have made several arrests in connection with an over $14 million attack on crypto protocol Holograph.
In a detailed post on X on Aug. 14, the omnichain tokenization platform stated that law enforcement authorities in France and Italy had made multiple arrests of individuals suspected to have been behind the theft of 1 billion of its native tokens, valued at 13 million euros (about $14.4 million).
According to the team behind Holograph (HLG), investigations into the incident were led by the Office for the Prevention of Cybercrime and the Brigade de Répression du Banditisme in France. It also got assistance from Europol, Italy’s Directorate of Anti-Mafia Investigations, and the Cayman Islands police.
French publication Le Parisien described the suspects as Eastern Europeans in their 30s, reporting that they had been arrested in Italy and were awaiting extradition to France. It was also said that authorities had seized electronics and frozen funds belonging to the suspects.
The hack occurred on June 13, with the attackers exploiting Holograph’s operator contract to mint a billion HLG tokens using a proxy wallet.
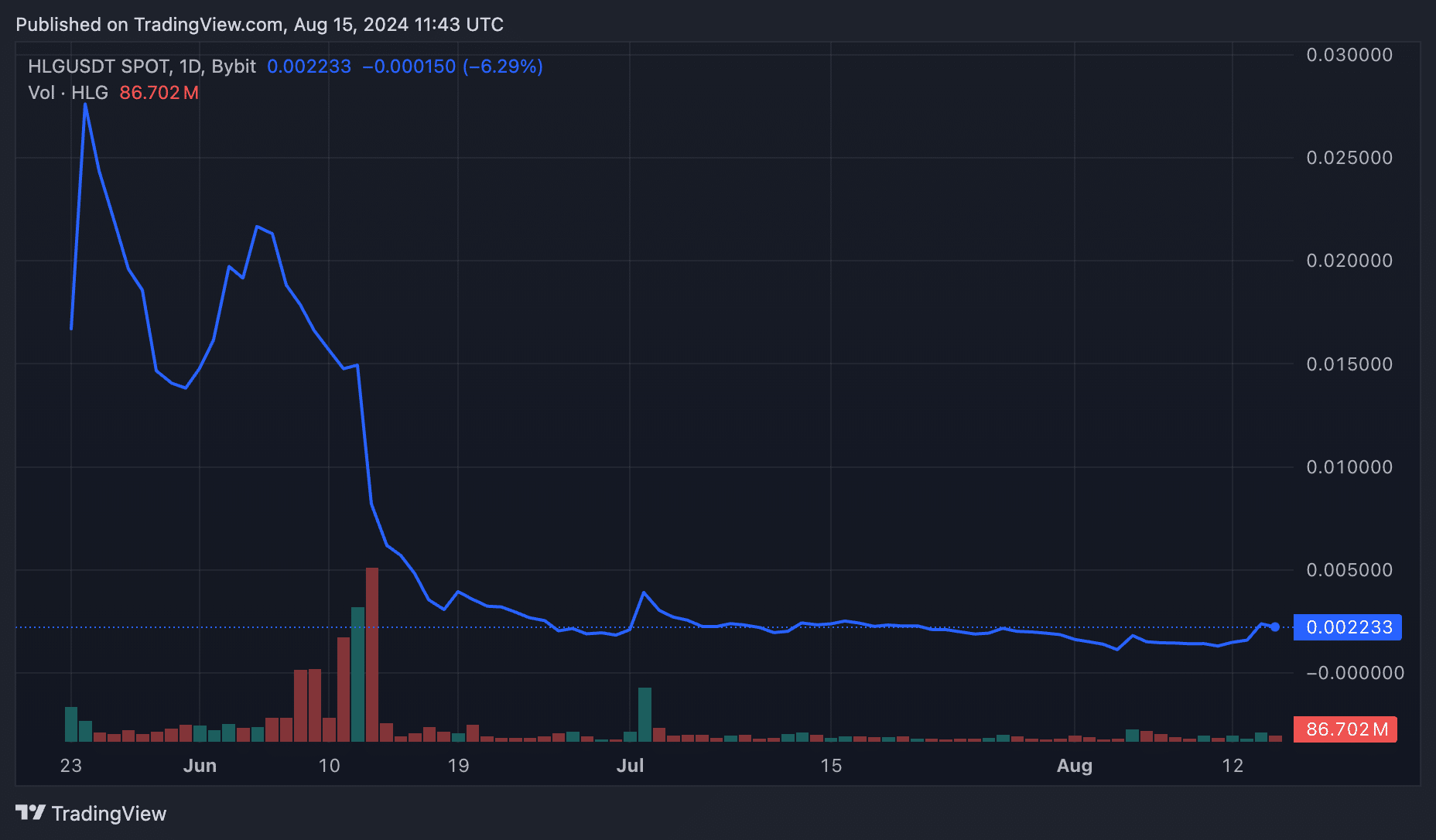
Following the incident, HLG lost more than 80% of its value, dropping to a low of $0.0029. Data from crypto.news shows that the token has mostly traded below $0.003 since the attack, only briefly hitting $0.049 on July 2, a date that coincided with Holograph’s release of a post-mortem report of the attack.
At the time of writing, HLG was priced at $0.00231, a 28% increase over the past 24 hours. The token is up almost 60% on the week.
The post-mortem found that a “disgruntled former contractor” of the platform was responsible for the exploit. The contractor allegedly used their administrator access to insert malicious jobs into the platform’s smart contract, which they then executed on June 13.
Additionally, data from Etherscan showed that the attacker converted the stolen funds into Tether (USDT) only hours after the exploit.
The platform has since then implemented operational risk controls aimed at preventing such incidents from happening in the future.