WLFI crypto holders targeted by phishing attacks at scale post launch
Experts warn that scammers are specifically targeting the hype around Trump’s WLFI token.
Summary
- Scammers are deploying phishing attacks at scale, exploiting the hype around WLFI
- Phishing attacks weaponize Ethereum’s new functionality, enabling wallets to act as smart contracts
- Ethereum’s EIP-7702 enables users to sign multiple complex transactions at once
The launch of World Liberty Financial (WLFI) cryptocurrency, linked to U.S. President Donald Trump, resulted in unprecedented hype. With volumes rivaling many of the biggest crypto projects, scammers were prepared to exploit the situation.
Shortly after the launch on Sept. 1, Yu Xian, founder of the blockchain security firm SlowMist, reported phishing attacks at scale. He explained that attackers are using new functionality built into Ethereum wallets introduced with Ethereum’s Pectra upgrade.
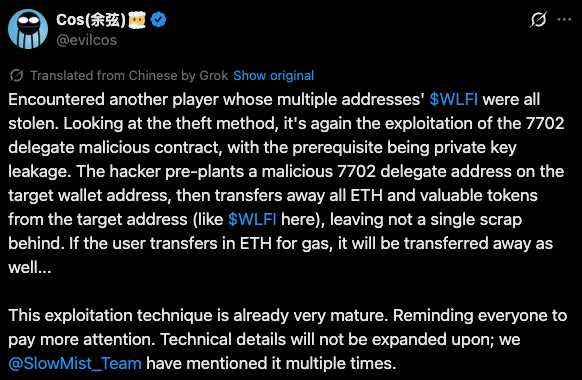
According to Yu Xian, the EIP-7702 “delegate” function enables external accounts to act like smart contract wallets. While this improves functionality, it also enables attackers to hijack the delegate mechanism if they compromise the private key.
How scammers target WLFI holders
The EIP-7702 “delegate” scam works as follows. The attackers first exploit a private key via phishing. Then, they embed a malicious delegate smart contract in the wallet. At that point, once a victim makes any transaction, the malicious code executes, draining the victim’s tokens.
The main reason attackers opt for the delegate scam is scale. Traditional phishing requires attackers to monitor and manually drain wallets. With delegate contracts, they can set parameters that auto-execute transactions, for instance to receive WLFI tokens via airdrop.
This is not the only type of scam that targets WLFI holders. For instance, attackers also try to trick users into buying fake WLFI tokens. In one case, attackers targeted one user who had bought WLFI tokens. They then airdropped honeypot WLFI tokens until the user accidentally bought a fake token on Phantom Swap. The victim lost $4,876 to the scheme.